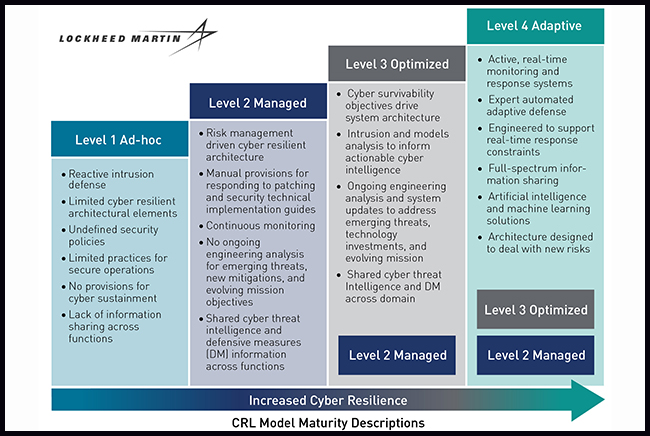
The graphic above, provided by Lockheed Martin, describes the Cyber Resiliency Level model. Lockheed Martin graphic.
Lockheed Martin wants the Defense Department to adopt its recently designed framework that shows how well a military system can hold up against cyber attacks, amid growing recognition that the Pentagon’s weapon and business software is vulnerable to 21st-century threats.
The contractor is using its “Cyber Resiliency Level” model on about 10 undisclosed test cases that include proposed, developing, and legacy military systems. Those pilots will wrap up by the end of 2019.
When those pilots end, Lockheed expects it will inform its military customers of the results so the findings can help shape the programs, Jim Keffer, cyber director in Lockheed’s government affairs office, said in an email.
“It would also give them the opportunity to establish a long-term arrangement to continuously measure the cyber resiliency of the system throughout its lifecycle,” Keffer said. “We will incorporate the lessons learned and best practices from each of the pilots to continue to advance the model.”
The risk matrix, which debuted last year and is now on its third version, breaks cyber resiliency into four categories defined by how a system approaches issues like cyber hygiene, test and evaluation, information sharing, and requirements. Systems that sit at levels three and four (“optimized” and “adaptive”) could be more complex weapon systems for which DOD wants less risk, while systems at levels one and two (“ad-hoc” and “managed”) could be less mission-essential systems that can take on more risk, like business software.
Dawn Beyer, a senior fellow and CRL project lead at Lockheed, said existing methods of assessing cyber risks can miss the mark if they are based on earlier requirements rather than the most current version of a system.
Lockheed sees its model as one potential piece of DOD’s attempt to change cybersecurity policies, guidance, and processes as military systems grow increasingly software-dependent. A 2018 Government Accountability Office report found that while the Pentagon is making progress, the department still “faces barriers that could limit the effectiveness of these steps, such as cybersecurity workforce challenges and difficulties sharing information and lessons about vulnerabilities.”